How Private AV Works
Explore its zero-retention architecture, dual verification modes, and real-time compliance logic.


Verification Process
Real-time estimation or full document review, with instant input deletion and anti-fraud analysis built in


Predicts user age from facial signals using trained models

Blocks still images and other non-genuine capture attempts

Protects against deepfakes and replay attacks with active analysis
.png)

Extracts and confirms ID data with OCR and structure checks

Compares live selfie to document photo for identity assurance

Supports audit logs for payout, AML, or jurisdictional reporting
.png)

Verification result is returned instantly. All biometric inputs are erased with no trace.
Seamless Emblem Integration
Built-in support for Emblem, the privacy layer behind regulator-approved tokenized checks.

Privacy-First Architecture
Engineered to eliminate retention risks. No biometric storage, no regulatory exposure, no breach surface.
Ephemeral Execution
Each request runs in an isolated environment that’s immediately destroyed
Volatile-Only Handling
Biometric inputs stay entirely in memory and are never written to storage at any point
Secure Data Destruction
Temporary assets are encrypted at rest and cryptographically shredded after use
Isolated Compute Enclaves
Verification sessions are fully sandboxed from other flows and customer environments
Private AV vs. Traditional Providers
See how our zero-retention architecture stacks up against legacy systems that store and expose user data
.png)

Built for Global Standards
Private AV meets regulatory requirements across the UK, EU, US, and other major jurisdictions
Supports frameworks from Ofcom, Arcom, KJM, COPPA, and other enforcement bodies
Outputs verifiable results without retaining personal or biometric data

Adapts by location — with built-in fallback handling, consent options, and minor protections

Designed to track and support evolving laws across Europe, the US, and Australia
Built for compliance standards everywhere
Two verification modes. One compliant system.
AI Age Estimation
Low-friction, low-cost face analysis for instant age screening. Can auto-escalate to document verification based on policy or risk.
.svg)
No accounts, no document uploads — optimized for conversion.
.svg)
Approved for low-risk scenarios under COPPA, KJM, and similar frameworks.




Full Document Verification
ID-based verification with face match, fraud screening, and audit-ready output — built for regulated and high-risk environments.
.svg)
Combines government-issued ID validation, facial comparison, and liveness detection.
.svg)
Supports GDPR, AML, and KYC obligations with traceable verification records.




Dual-mode verification, built for flexibility
Use face-based estimation, ID-based checks, or both — depending on jurisdiction, content type, or risk profile. Private AV lets you adapt verification logic across flows, all within a privacy-first, zero-retention system.
Frictionless Age
Check
Secure, ID-backed verification
Enterprise-Grade Analytics With No Personal Data Stored
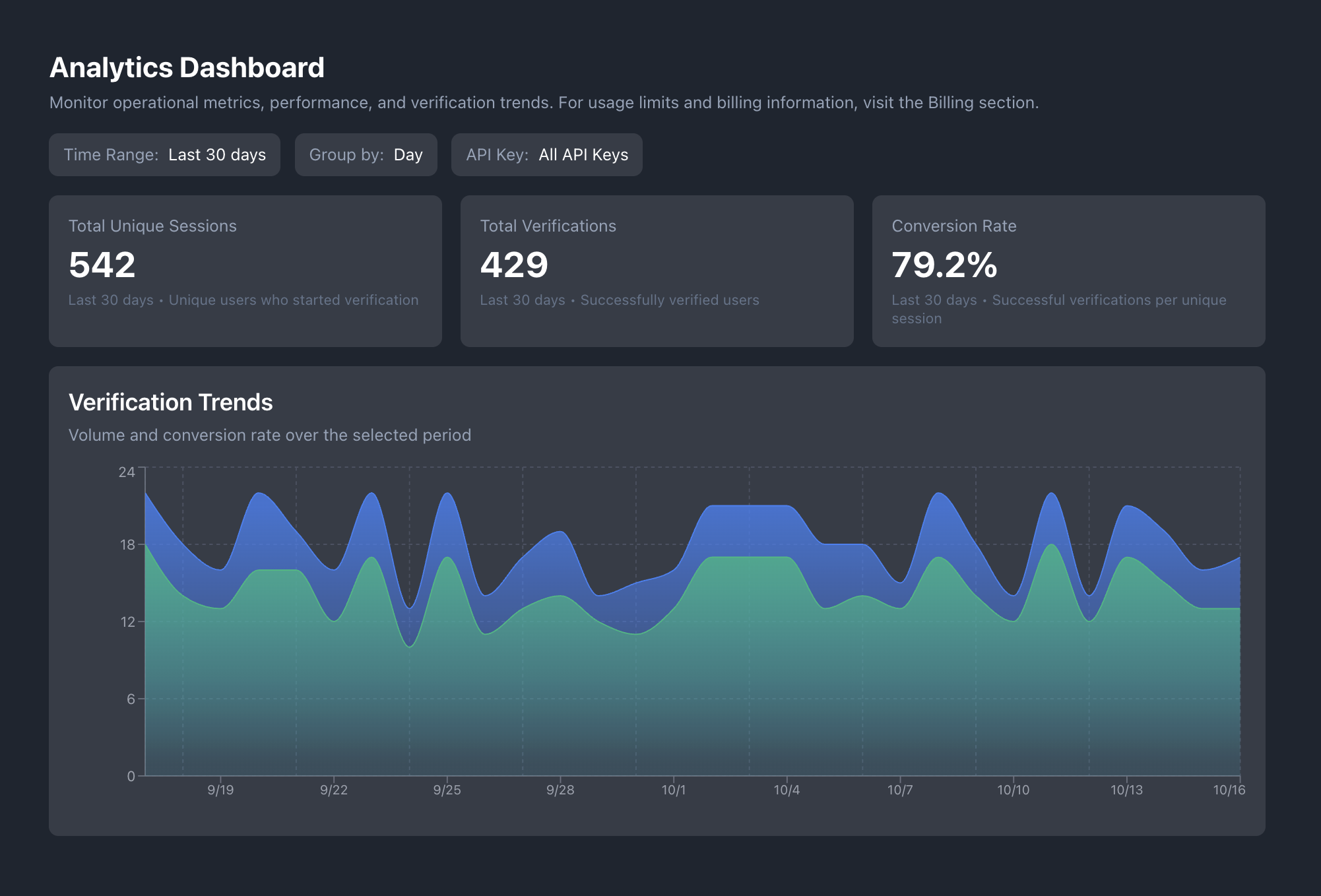
Operational Monitoring
Track active verifications, real-time outcomes, and liveness results in real time

View submission rates, completion stats, and pass/fail breakdowns by flow type
Compliance & Reporting

Generate structured logs to support GDPR, COPPA, KJM, and KYC audits

Analyze verification traffic by region to support local compliance requirements
Fraud & Infrastructure

Identify device spoofing, high-frequency attempts, and repeat abuse patterns

Monitor latency, uptime, and error rates across all deployed integrations
Ready to Deploy. Easy to maintain.

Just 17.6KB, framework-independent, and compatible with major web stacks

Integrates in under 5 minutes. Includes sandbox mode, test credentials, and full docs

Encrypted callbacks, strict isolation, and no storage of user data on your system

Customize the verification flow to fit your UX and branding — layout, logic, and styling

Frequently Asked Questions
It defaults to L1 (face-only checks) and escalates to L2 (document-based) only when required — reducing friction and limiting data exposure.
Yes. You can configure rules for L2 escalation, minimum verification ages, and country-specific flows.
Standard protections include liveness checks, face-to-ID matching, and multi-signal fraud detection.
L2 captures and parses ID data, checks format and validity, and matches against a selfie — all in-session, with no data saved.
No. All processing is ephemeral. Inputs are deleted immediately after verification completes — nothing is retained.
Yes. Use the sandbox to run 100 test verifications with full webhook support. Production plans include 500 free live checks.